- 25
Aug - 2017Hacking
2 min | 2095Yesterday I received an email from an address that should look like my boss email address. It was something like this: "Boss.Name@our-institute.uni-hannover.de nancy@hillstar.brcoxmail.com" with the subject:
Rech QK - 163-DA7666 Riva, Mauroand a text saying:Guten Tag, Riva, Mauro Als Anhang erhalten Sie Ihre Rechnung. (something like "You receive your invoice as an attachment.") Rech: http://blackbox-es.com/Rechnung-26375407950/ (don't click this link --> read all the post!!!) Herzliche Grüße (Grüße: Grüße) boss.name@our-institute.uni-hannover.deAs you see, there is a link to the Blackbox-ES company website based in Kaysville, UT, USA.
You are obviously going to say phishing! That's for sure! But I clicked on the link to check it out! I used a Tor browser (I didn't want to give my IP). The link started a download of a word document with name
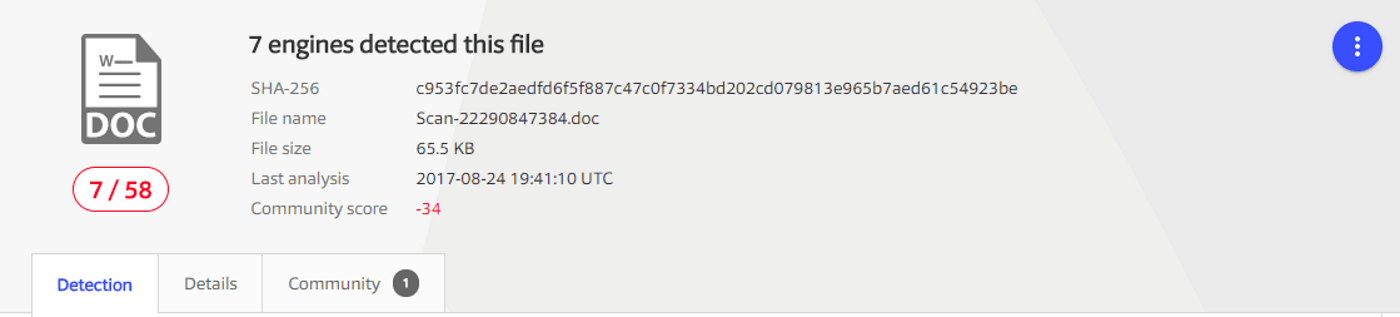
Rechnungs-Details-43154391936.doc, and again obviously with macros inside!: A payload! I haven't opened it yet, but I am going to use a virtual machine this weekend, that I usually use for that. I want to read the payload and if it's possible check the remote host address.I uploaded it to VirusTotal and at first time (yesterday at 10 a.m.), only 4 antivirus were able to detect the file as a threat! Now, I uploaded it again and I got the following report:
![Macro Virus]()
VirusTotal report Only 7 antivirus detect the file as a threat! I still have the file on my download folder and the Microsoft Security Essentials is not reporting or deleting it!!! Nice! :S
I've done the following things:
- I've reported the link as phishing to https://safebrowsing.google.com/safebrowsing/report_phish/
- I've written to the company contacts to inform about the file (I hope it will be deleted any time soon!)
- I've opened report cases on:
I found the following report: https://goo.gl/yPakSa It contains more information about the payload!
(I haven't check the email
nancy@hillstar.brcoxmail.comyet, but it probably doesn't exist neither the domain)We will see tomorrow!
Notes:
- (1) I've just received an email from Kaspersky Lab with following content:
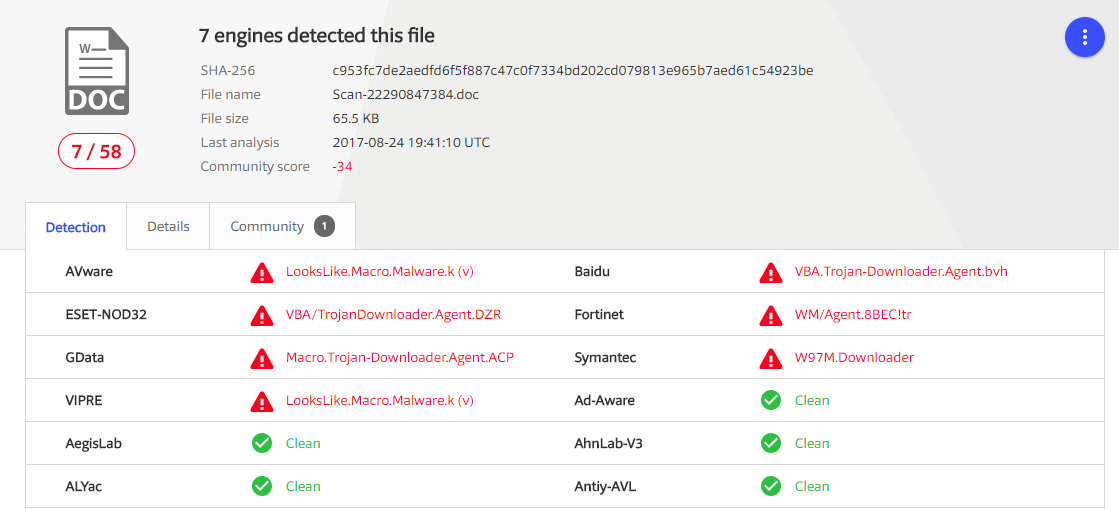
Malicious code detected by Kaspersky Lab products with KSN technology enabled has been found in the following files: Rechnungs-Details-43154391936.doc - UDS:DangerousObject.Multi.Generic - (2) Microsoft reports the following:
![Microsoft Report]()
Updates:
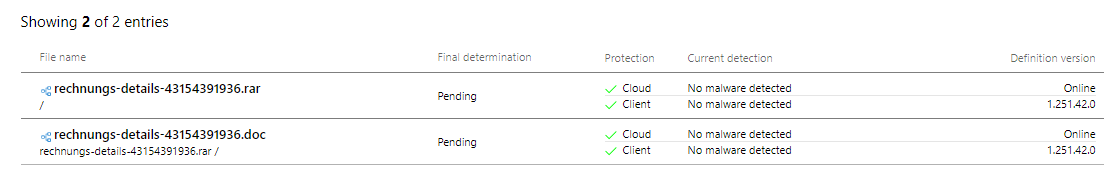
25.08.2017 10:20: 11 Antivirus (Microsoft still reports the file as clean!)
![Update 20170825 10:20]()
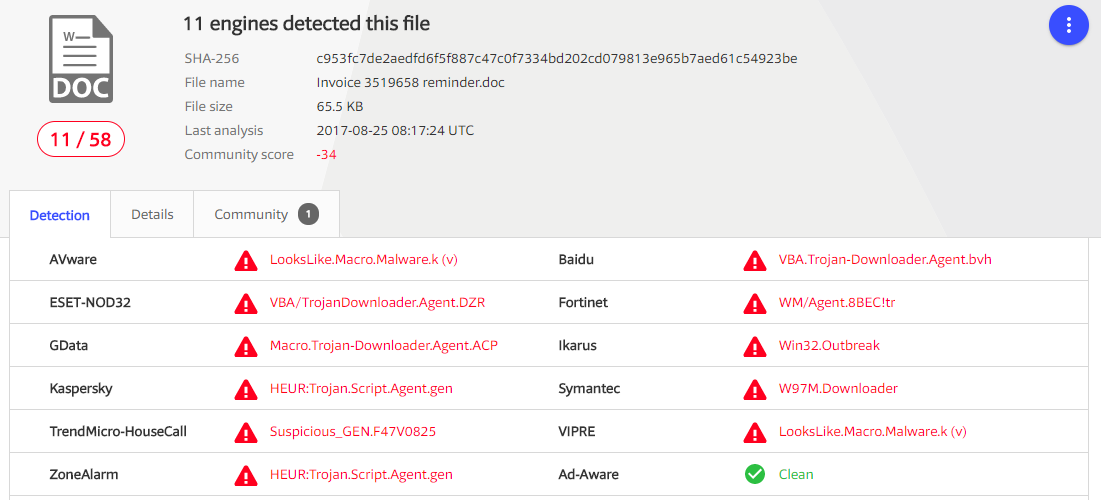
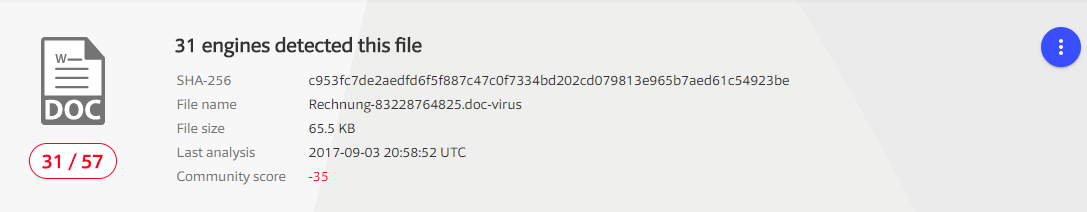
Last update (03.09.2017 23:00): 31 Antivirus (Microsoft still reports the file as clean! I've submitted it twice, but no chance!)
![Last Update 20170903 23:00]()
We use cookies to improve our services. Read more about how we use cookies and how you can refuse them.
Empty