- 04
May - 2022Product Reviews, Raspberry Pi
4 min | 11294Last December, I wrote an article about the crowdfunded "High Resolution Autofocus Camera Module" for Raspberry Pi from Arducam. That camera costs only USD25 and has autofocus and a resolution of 16 MP. You can read more about it here: Raspberry Pi: ArduCAM powerful $25 camera with high resolution and autofocus.
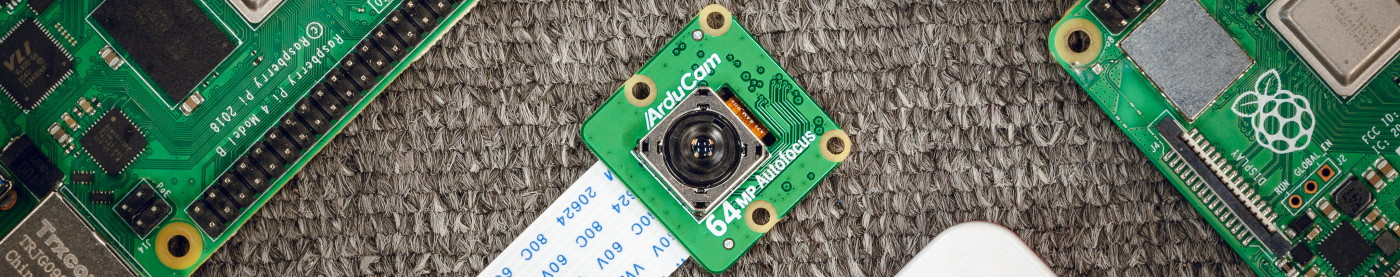
Last week, I got a sample of the new Arducam Hawk-eye camera. The camera module also has autofocus but the resolution has been improved to 64MP and it’s available from the Arducam store at a pre-order discount (
$59.99$35.99 as I'm writing this article). Let's start with the review of ...16
Jan - 2022Home Automation, Raspberry Pi
12 min | 146837#Home Assistant: DIY Smart Home - tips and tricks (SSL, HAProxy & Let's Encrypt)
Home Automation, Raspberry Pi | 12 min | 146837
In the last years, I wrote several articles about Home Assistant (HA) and the possibility to replace the Zigbee hubs from different companies in your home using Zigbee2MQTT. Some of those articles are listed here (don't visit the links, they are outdated):
08
Jan - 2022MicroPython
5 min | 36047Last week, I got some time to update the
lemariva/micropython-camera-driverto the actual versions of MicroPython, ESP-IDF, and the camera driver for the OV2640. MicroPython has changed since version 1.14 frommaketoCMakewhich makes it easier to add support for different modules: in this case for the OV2640.I will sum up the steps to compile MicroPython fr...
10
Dec - 2021Product Reviews, Raspberry Pi
4 min | 38520#Raspberry Pi: ArduCAM powerful $25 camera with high resolution and autofocus
Product Reviews, Raspberry Pi | 4 min | 38520
The Raspberry Pi cameras are getting cheaper but they are not losing quality and performance. At least that is the claim of the company ArduCAM and the Crowdfunding campaign on Kickstarter. I got a sample, let's start with the review!
The campaign has now moved to indiegogo: Check out this link: 16MP Autofocus Camera Module for Raspberry PiArduCAM company is located in China and dedicates to designing and manufacturing open-source hardware and software s...
30
Sep - 2021MicroPython, Product Reviews
2 min | 18063#M5Stack Tough: A weatherproof ESP32 Industrial IoT controller
MicroPython, Product Reviews | 2 min | 18063
M5Stack has launched several ESP32 IoT controllers with an integrated touch display such as the M5Stack Core2, the M5Paper, etc. Today, a new Core family member was presented: the M5Stack TOUGH. This device is rugged and dustproof/waterproof with a UV-resistant enclosure sealed with an o-ring and offers waterproof M12 connectors. M5Stack TOUGH is now available for purchase for $49.90 on the company’s store (check out the link below).
The protection against solid ...
13
Aug - 2021M5Stack, MicroPython, Product Reviews
1 min | 18584#M5Stamp Pico: an ESP32 miniature and powerful module
M5Stack, MicroPython, Product Reviews | 1 min | 18584
M5Stack is a technology company based in Shenzhen China, which specializes in the design, development, and production of IoT development toolkits and solutions, and today they have just launched a new device in its core series: the M5Stamp Pico; and awesomeness comes in small packages.
I thought the M5Stack ATOM would be the smallest core possible, but I was wrong!. The M5Stamp Pico is even smaller and still very powerful. The M5Stamp is the smal...
05
Apr - 2021Raspberry Pi
1 min | 28211#Raspberry Pi: Amazon Prime, Netflix, Disney, Spotify - a DRM official solution
Raspberry Pi | 1 min | 28211
Last June, I published an article about installing a DRM solution for the Raspberry Pi. If you don't know much about Widevine DRM, I'll quote my last article:
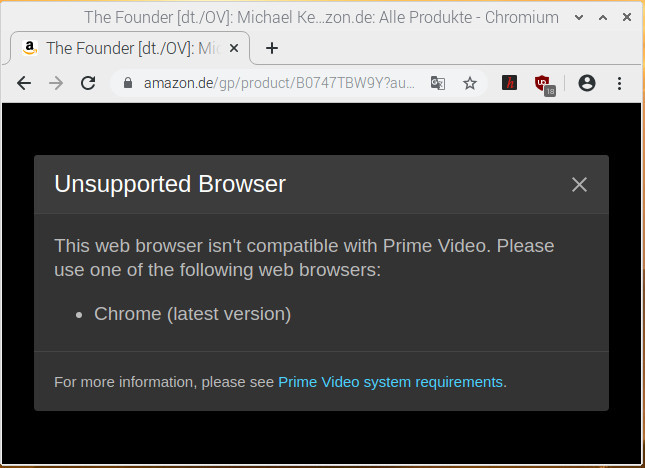
It is a rainy day and you have a Raspberry Pi, which is running Raspberry OS (Raspbian), and you think: I can make a media center to watch some movies/series. You configure everything, and then you see something like the next picture, every time that you want to watch Amazon Prime, Netflix, etc. using the Chromium Web Browser:
![]()
Fig. 1: Trying to play Amazon Prime videos on the Raspberry Pi running Raspberry OS. DIY Instruc...
03
Apr - 2021Product Reviews
2 min | 17940#Crowbits: Programmable Blocks for STEM Education (ESP32, Arduino and Micro:bit compatible!)
Product Reviews | 2 min | 17940
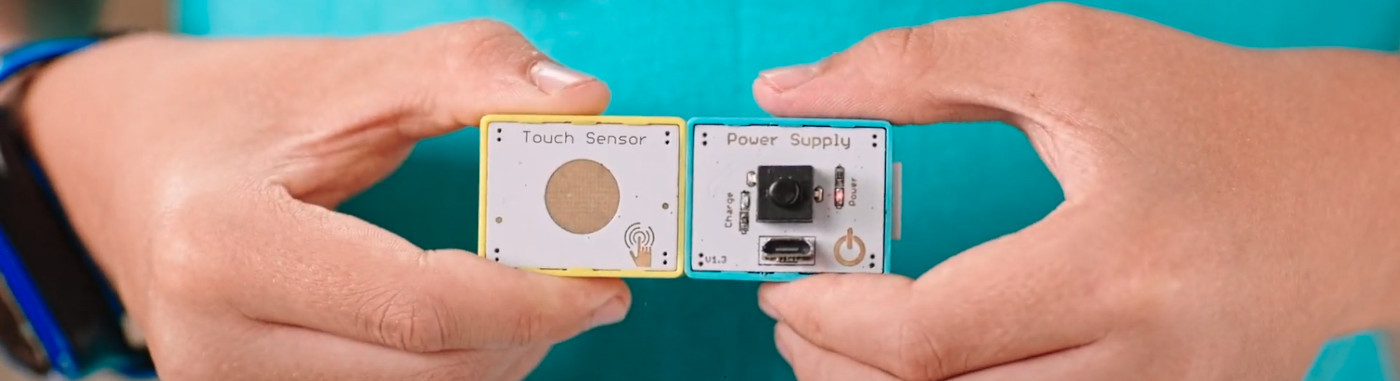
Late last year, I posted an article about the Elecrow CrowPi2. The laptop integrates plenty of electronics modules and I will be publishing a review later this month. But, this article is about the Crowbits. The folks at Elecrow are great and they have launched the Crowbits magnetic electronic blocks for STEM education, and the devices are ESP32, Arduino, and Micro:bit compatible.
![Playing with Crowbits]()
Fig. 1: Playing with Crowbits There are over 80 programmable electronic magnetic modules and bricks (see Fig. 2), with three different sizes ( large, middle, and small modules) and colors that indica...
15
Feb - 2021LoRa/LoRaWAN, MicroPython, Raspberry Pi
5 min | 41212#Raspberry Pi Pico: The RP2040 meets LoRaWAN
LoRa/LoRaWAN, MicroPython, Raspberry Pi | 5 min | 41212
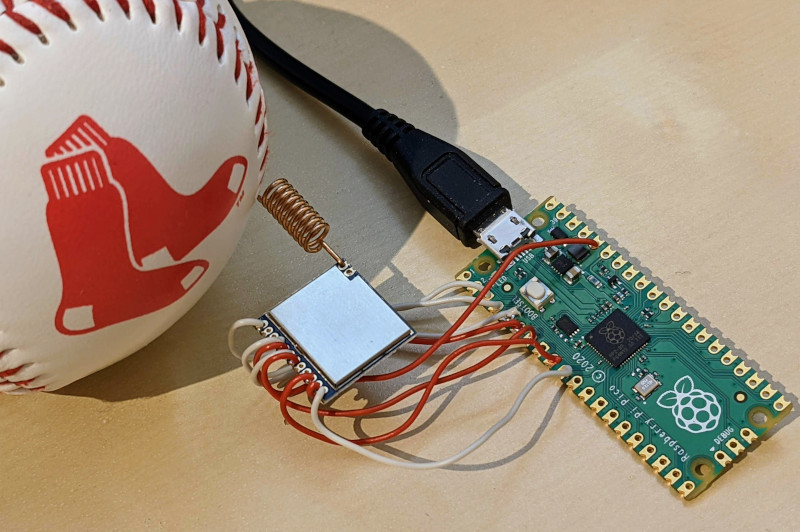
The "Pico" board with the RP2040 chip developed by the Raspberry Pi Foundation is the latest tiny fast and versatile board in Arduino Nano format. As you may already know, the board can be programmed using MicroPython and C/C++. In this tutorial, I extended the official MicroPython version to support cryptographic primitives, and this unlocks the possibility to connect the board (using the SX1276 chip) to the "The Things Networks" (TTN) - which means LoRaWAN support.
![]()
Fig.... 31
Dec - 2020M5Stack, Raspberry Pi
7 min | 480020#Raspberry Pi HQ Camera: Autofocus for the Telephoto Lens (JiJi)
M5Stack, Raspberry Pi | 7 min | 480020
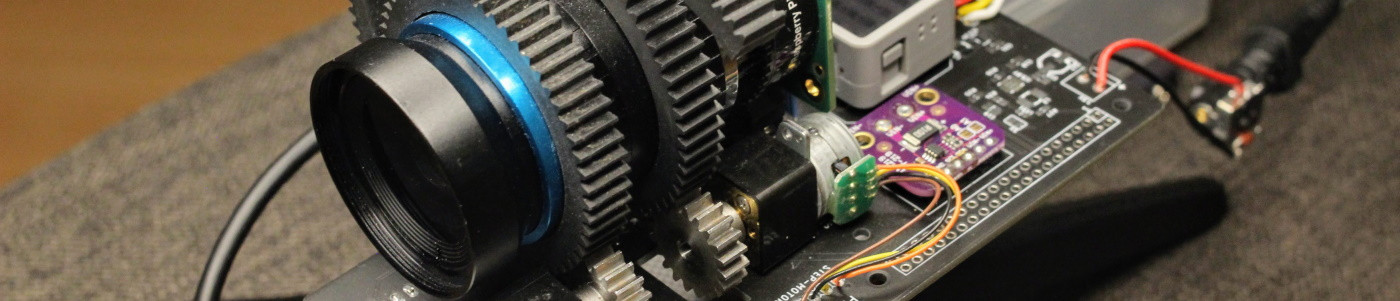
This tutorial opens the series of articles about "Project JiJi" and describes how to add autofocus to the 16 mm Telephoto Lens mounted on the Raspberry Pi HQ Camera. In the past months, I've been working on a project to add autofocus to the lens and this is the result:
Adding some background to this: The Raspberry Pi Foundation offers different Raspberry Pi Camera modules since 2013. The first module (5-megapixel) was produced in 2013, and an 8-megapixel module upgrade (...
27
Nov - 2020M5Stack, MicroPython
2 min | 24458M5Stack has just launched a new device in its core series. This time, the company has combined two great things into a great product: a 4.7" EINK screen with touch capabilities and an ESP32 with 8MB PSRAM. As usual, the device is compatible with Arduino, MicroPython, and UIFlow. It only costs USD69,00.
The M5Paper is a fully programmable and portable device, which is an ideal choice for an IoT application (or you can just use it as an E-reader). The touch EINK screen can b...
15
Nov - 2020Cloud Platforms, M5Stack
2 min | 15044#M5Stack: Widgets on your Smartphone help you to stay safe from #COVID-19
Cloud Platforms, M5Stack | 2 min | 15044
This is the last follow-up of the tutorials:
- M5Stack: Fresh air checker helps you to stay safe from #COVID-19 and,
- Nginx: Docker, Flask and Let's Encrypt (SSL),
in which I explained how to build a CO2 measuring device using a M5Stack and an SG30 sensor, send the data to GCP, and offer it using HTTPS.
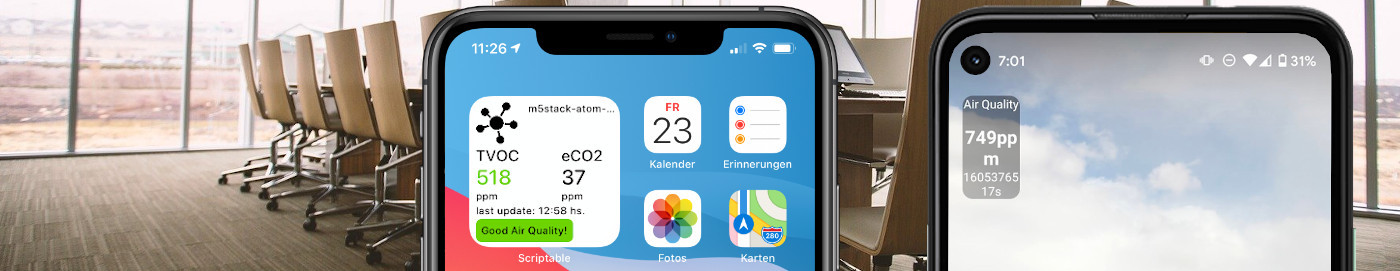
![CO2 reporting widgets on Android and iOS.]()
Fig. 1: CO2 reporting widgets on Android and iOS. These sensors can help to prevent Covid-19 spread in a room. If you want to implement the complete pipeline, check out the links above. This tutorial connects the data to your Android or iOS phone to see that in a Widget (see Fig. ...
15
Nov - 2020Cloud Platforms
5 min | 23302This tutorial is a follow-up of M5Stack: Fresh air checker helps you to stay safe from #COVID-19, in which I explained how to build a CO2 measuring device using M5Stacks and SG30 sensors. These sensors can help to prevent Covid-19 spread in a room. The collected measurements were sent to the Google Cloud Platform and a microservice offered them on a Website or a RestAPI using HTTP. This tutorial adds an
Nginxmicroservice to offer the Website and RestAPI over HTTPS.Let's start with some explanation about how HTTPS works: The encryption and security functionalities for HTTP are implemented thr...
15
Nov - 2020Cloud Platforms, M5Stack, MicroPython
12 min | 237874#M5Stack: Fresh air checker can help you to stay safe from #COVID-19
Cloud Platforms, M5Stack, MicroPython | 12 min | 237874
Winter is coming and the air-quality inside a closed room could be an index used to estimate the amount of aerosols in it, and hence the risk of Covid-19 infection. In other words, a system of CO2 traffic lights could help to spot potential corona-aerosols!
Where there are many people in a room, there is a lot of exhalation (approx. eight liters of air per minute per nose). This air contains CO2 (carbon dioxide). Long before Covid-19, in Germany, the German Environment Agenc...
17
Oct - 2020General
5 min | 38037Last week, I was working on a C++ application on a remote machine in the cloud, and I didn't want to install all the compiling and debugging tools/libraries/dependencies on the host OS, but I wanted to have all of them in a container. I found that VSCode has the capability to target a container for application building and/or debugging :).
This article is a documentation for me that I will use every time that I need to compile a C++ application. The steps are divided in three main groups:
- You need to build a Docker image with the tools/dependencies/libraries etc.. A container will be started...
Subscribe to our mailing list:
We use cookies to improve our services. Read more about how we use cookies and how you can refuse them.