- 03
Nov - 2017Hacking
2 min | 1610And once again! Word files with Macro! But this time, I was the first one to report it to VirusTotal and Hybrid-Analysis! :)
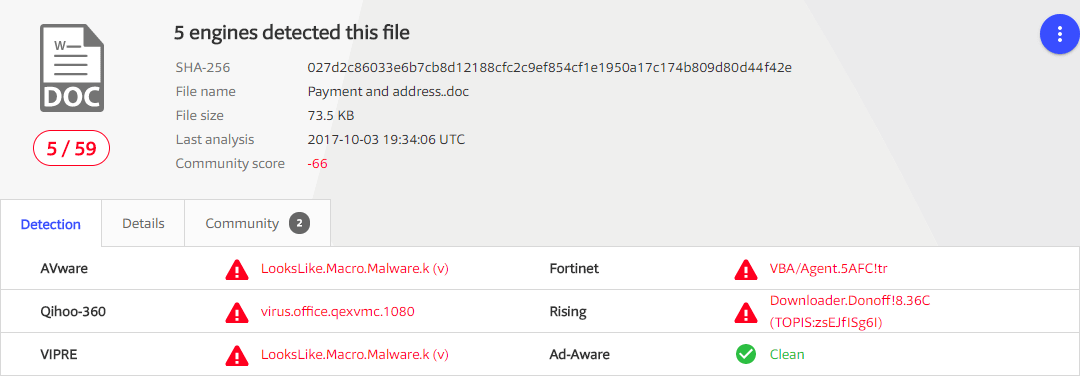
![Virus Macro!]()
Fig 1: VirusTotal report! Just only two: Fortinet sells hardware, and Qihoo-360 is in China (:S)... Here you have the e-mail. The sender is this time the "BOSS Last Name" (A nice improvement! :P) without address, or something like that!
Guten Tag, Riva, Mauro Bitte die gekennzeichneten Stellen ergänzen und unterschreiben, bitte mit Stempel außer das SEPA Formular. Für die Abbuchung. http://docs.google.de/download/de_DE/doc/ -> with hyperlink (http://elprofedemicurso.es/vago1n2a947ma/) Mit freundlichen Grüße, BOSS Last Name, BOSS First NameThe mails are being sending from a server in USA
coxmail.comand using the userrandy@cobianusa.com. Sorry randy, I published your e-mail! The auth is still PLAIN! I do not understand this!. Here you can see the logs:Thu, 2 Nov 2017 08:55:12 +0100 (CET) Received: from dukecmfep04.coxmail.com (dukecmfep04.coxmail.com [68.99.120.39]) by mfilter-112-2-1.mx.srv.dfn.de (Postfix) with ESMTP for xxxxxxx; Thu, 2 Nov 2017 08:55:11 +0100 (CET) Received: from dukecmimpo01.coxmail.com ([68.99.120.134]) by dukecmfep04.coxmail.com (InterMail vM.8.01.05.08201-2260-151-120-20120517) with ESMTP id <20171102075506.KWUW8337.dukecmfep04.coxmail.com@dukecmimpo01.coxmail.com> for xxxxxxx; Thu, 2 Nov 2017 03:55:06 -0400 Received: from 10.0.0.47 ([202.14.85.241]) by dukecmimpo01.coxmail.com with bizsmtp id Uvuo1w0015CQpq201vv35M; Thu, 02 Nov 2017 03:55:05 -0400 Authentication-Results: coxmail.com; auth=pass PLAIN smtp.auth=randy@cobianusa.com From: BOSS Last Name, BOSS First Name <randy@cobianusa.com> --only in details you can see the e-mail address! To: <xxxxxxx>(
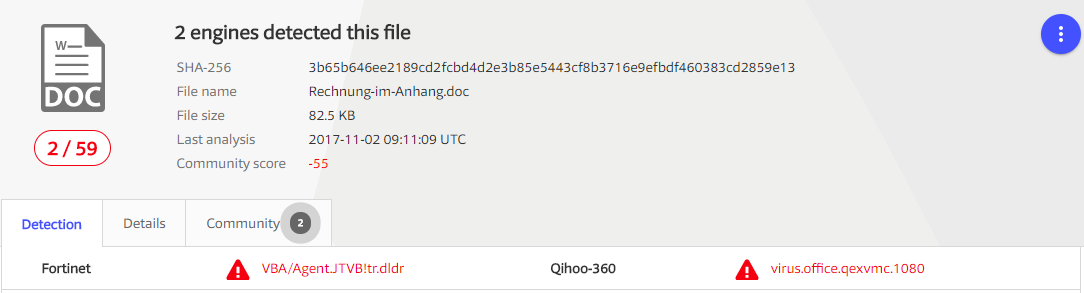
xxxxxxxmy work e-mail address -you can find it on the internet, if you want to...)Here you have the analysis of the files:
The analysis by Hybrid-Analysis is quite interesting! They were able to catch the host server:
Contacted Hosts IP Address Port/Protocol Associated Process Details 37.9.175.9 OSINT 80 TCP powershell.exe (PID: 3752) Slovakia (SLOVAK Republic) 217.13.106.249 8080 TCP storagewmi.exe (PID: 3036) HungaryThe standard correction language of the file was set to russian language.
As usually, I wrote 'elprofedemicurso' and I sent the files to the Antivirus companies. Avira still does not recognize the file as a VIRUS!!! :( .
I've read somewhere that they are using ObfuscatedEmpire to obfuscate the files. There are little chances for the Antivirus to detect a new variant of this type of files. That means, I am going to receive more e-mails like this one, or I should I have to tune the Spam filter! Do you have an idea how can I filter this type of e-mails using Exchange 2010?!. Please write me a comment, if you known that! Thanks in advance!!!
We use cookies to improve our services. Read more about how we use cookies and how you can refuse them.
Empty